These days, people are starting to get aware of the risks they face while using modern technology. Still, while many users think they are perfectly safe when using the often prescribed security measures like antivirus software and firewalls, they are in fact not. The Pupy RAT is just one example of a cyber threat that could easily hit you in the face when you don’t expect it.
Remote Administration Tools
Let’s start with a bit of context. Imagine you are a hacker and you want access to someone’s computer. The point is, many people are safely behind a firewall which will not allow you to attack their system directly. That is where so-called Remote Administration Tools (RATs) come in.
A RAT is a piece of malware that, once running on a target computer, enables a hacker to remotely control it. This means that somehow, the hacker needs to get the RAT on the victim’s computer. Once that is done, the RAT will ‘call home’, meaning it will tell the hacker’s computer it is running on a machine and that it is ready to execute any commands. The hacker can then use this connection to send whatever command he would like to execute, resulting in him being able to browse the file system, open programs, take screenshots, use the webcam, etc. The victim is now completely hacked, and the hacker can do exactly the same stuff he would be able to do when he would be sitting in front of the computer physically.
The hacker’s side of the RAT consists of a service that accepts incoming connections (the ones being launched from the victims), and some kind of a dashboard in which all the infected computers can be viewed and controlled. Using this interface, a hacker can easily control thousands of computers at the same time.
Pupy RAT
On 21 September 2015, Reddit user n1nj4sec posted a link to the source code of a RAT he had created. He called it Pupy, and posted screenshots of how to easily deploy this RAT and use it without leaving any traces on the victim’s computer. Without going into too much detail here, the RAT could infect and then act like any genuine service that always runs on the target’s operating system, and would remain undetectable for antivirus software this way.
After doing a couple of simple, local tests, it turned out that it was indeed ridiculously easy to bypass both antivirus and the firewall and completely own any computer. Even after updating the antivirus software running on the test machine, it would not even detect the executable file used to infect the computer itself.
While some other antivirus suites did detect Pupy, it is important to keep in mind that the RAT will behave like any other program on your computer; it will connect to the internet exactly the same as, say, Spotify or Internet Explorer would. This makes it hard to distinguish the RAT from genuine software. After all, the victim was the one who told the computer to run the program. Generally speaking, tools like this will only be recognized by antivirus software if they are in their list of malicious programs. Changing the source code (and thus the entire program) just a tiny bit could evade this in many cases.
A simple use case
How realistic is this, and how easily are you infected? Let me show you a simple example:
A family member sends you a vacation photo by email. Once you download the attachment, you see a filename that looks valid at first sight. Say it looks like the file in the following example:
![]()
While this attachment might seem like a legit image, a closer look shows it is in fact not a .jpg file, but instead just has tens of spaces in the filename, followed by the real extension: .exe.
![]()
A simple trick like this might trick you into opening it. Keep in mind that executing it only once is enough to be completely hacked. For the hacker, now, the rest is peanuts. In the screenshot below, he takes a snapshot with your webcam (some details redacted):
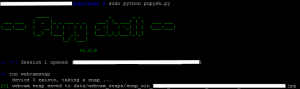
Now let’s say you have a copy of your passport, some credit card details or a ‘handy’ list of the passwords you always use stored somewhere on your computer. Let’s also say you are the director of some company others might be interested in. What can happen from this moment on? I will leave that up to your imagination…
1 Comment