Some 1,5 years ago, I wrote a really basic article about Pupy (an open source RAT). In an on-site CTF I participated in yesterday, I found it quite useful in a challenge that required dumping NTLM hashes of a Windows user.
The context
In the challenge before, the password of the ‘administrator’ user that was reachable through RDP had to be cracked. In this post I provided a short tutorial on doing exactly this.
In this challenge, the description stated that there was another admin user on the system, and its NT hash needed to be dumped.
Getting the hashes
In Windows, the NTLM hashes are located in the SAM file, which is located in C:\Windows\System32 and in the registry (at HKEY_LOCAL_MACHINE\SAM). However, for obvious reasons, Windows did some work to prevent you from opening and dumping these files while the system is booting. This means it is possible to boot Linux on the machine and dump the SAM file, but only if you can switch it off and have physical access to the machine. In this case, that approach was simply not an option as the machine could only be reached through the network.
As we have the username and password of the ‘administrator’ user, we should be able to launch a meterpreter shell through Metasploit and run hashdump from there. However, it took me too long to get the reverse shell to successfully connect back to my VM. Instead of trying to fix it any longer, I decided to take another route after I remembered the awesome open source Pupy RAT.
Using Pupy
Through the RDP session on the remote machine, I downloaded a Pupy payload I had created before. After the payload was executed (no antivirus or firewalls blocked it), it connected back to my Pupy server without any problems.
From the Pupy server, I ran the command ‘creddump’ (the screenshot below was made without the client connected, but gives an idea of what it looked like):
The ‘creddump’ module did its work, and showed the NTLM hashes successfully!
s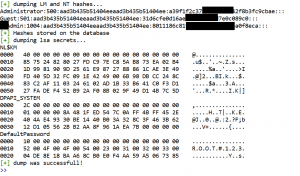
Other interesting tools
Pupy comes packed with a whole load of modules. One module I find particularly interesting is an implementation of the open source tool LaZagne, which enables you to dump all cleartext passwords stored on the infected machine. Again, only use this for CTFs or pentest engagements if there is explicit consent from the target!!